Some of the Bugcrowd Engagements utilize Cloudflare Zero Trust in order to provide secure access and also log researcher traffic on the customer’s assets. In those cases, the researchers are required to use Cloudflare Zero Trust every time to test against the customer’s assets in those engagements. Researchers should ensure that they are logged in to the Cloudflare Zero Trust WARP client for that customer organization while testing.
The engagement brief will provide the following information to set up the WARP client:
- Link to download the Cloudflare Zero Trust WARP client: Download WARP Client
- For more information on the Cloudflare Zero Trust WARP Client, visit the Cloudflare Zero Trust WARP Documentation.
- Team name:
customername-bugcrowd - Review and Accept the T&Cs
- User ID : Your assigned Bugcrowd Ninja Email ID
- Confirm with the OTP you’ve received via your Bugcrowd registered email address. This should launch the WARP client.
- Disconnect from the WARP client once testing on this engagement is completed.
Note: It is required to connect to CFZT every time you test the assets in this engagement. (Note that the targets might still be accessible publicly but the rules of engagement for this customer require that you use CFZT).
Submissions without clear use of CFZT will not be accepted.
Step-by-step instructions to set up and access through WARP client
Download the WARP client using the link provided in the Engagement brief
-
Open a Warp Client.
-
Open Preferences → Account.
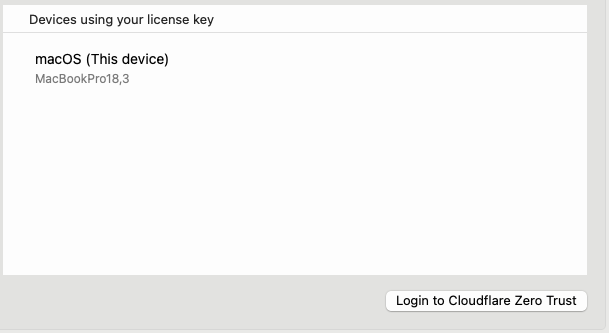
- Click on Login to Cloudflare Zero Trust.
- You will be asked to enter the Team name; Copy and enter the Team name provided in the Engagement Brief
- After typing the Team name, you will be redirected to log into the Cloudflare Zero Trust app
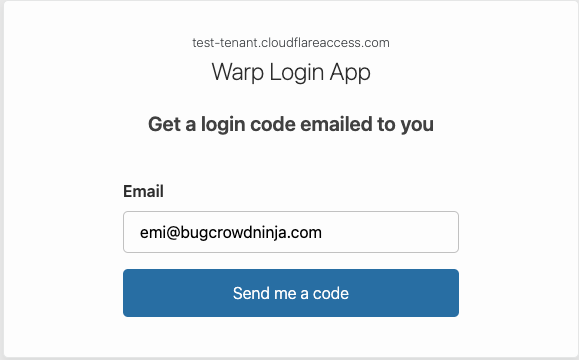
- A one-time pin will be delivered to your account.
-
Once the pin is confirmed in the browser, the WARP app will launch and log into Zero Trust.
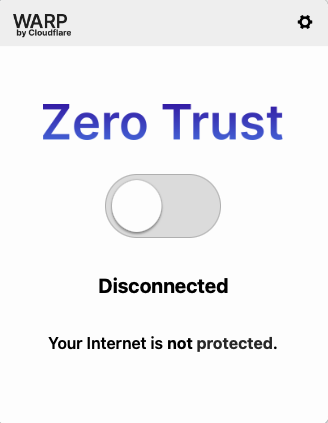
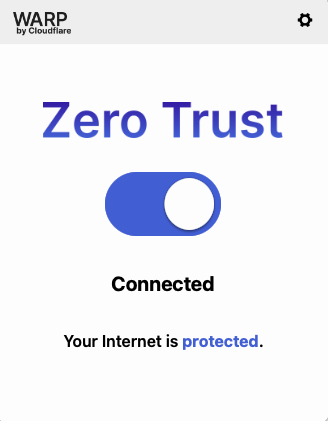
Please note that Engagements that utilize Cloudflare Zero Trust, log researcher traffic on the customer’s targets specified in that Engagement. The following information about the activities is logged in the log file:
| Field in the Log file | Details |
|---|---|
| Datetime | Date and Time of the HTTP request made |
| URL | Full URL for the HTTP request |
| Email ID of the user who made the HTTP request, through the WARP client | |
| HTTP Host | Hostname present in the HTTP header for the HTTP request |
| Action | Action taken based on the first rule that matched (for example Allow or Block) |
| HTTP Version | HTTP version of the origin connected to on behalf of the user |
| HTTP Method | HTTP method used for the request (for example, GET or POST) |
| HTTP Status Code | HTTP status code returned in the response |
| Destination IP | Public IP address of the destination requested |
| Destination Port | Port of the destination requested |
| User Agent | User agent header sent in the request by the originating device |
| Untrusted Certificate Action | What action should be taken if an untrusted origin certificate error occurs (e.g., invalid certificate chain, signed by non-public CA, expired certificate, etc.) |
| Session ID | The session identifier |
| Referrer | Referrer request header containing the address of the page making the request |
