If you do not have OneLogin set up, see getting started guide.
Specific Role Required to Configure SSO: To configure SSO for your program, you must be an Organization Owner. Organization Owners can log in using Username and Password.
Adding Bugcrowd to Your OneLogin Apps Portal
-
Log in to your OneLogin account.
-
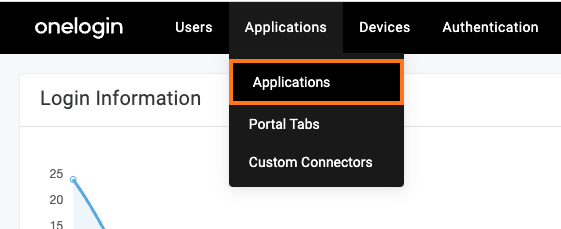
Select Applications > Applications
-
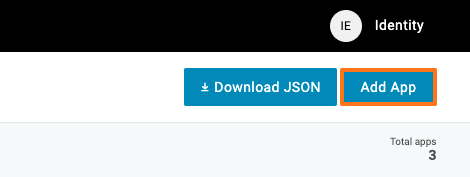
Click on Add App on right corner.
-
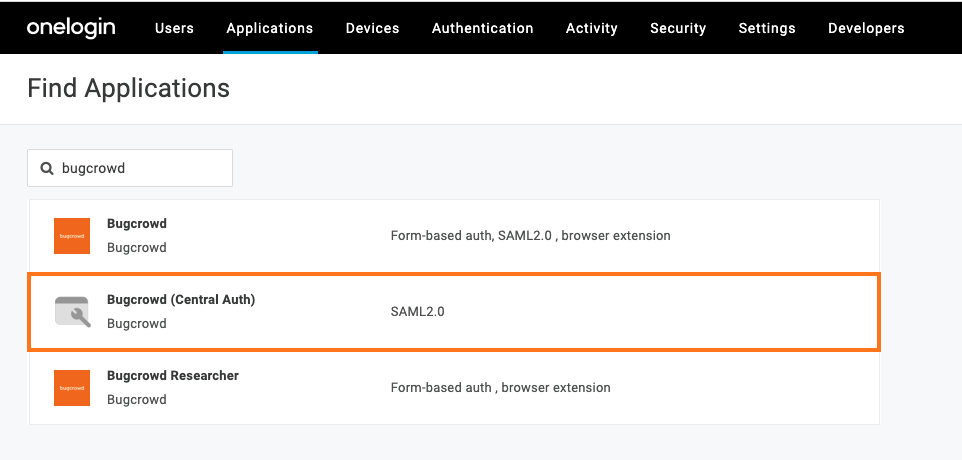
Search for Bugcrowd.

-
Select the Bugcrowd (Central Auth) app.
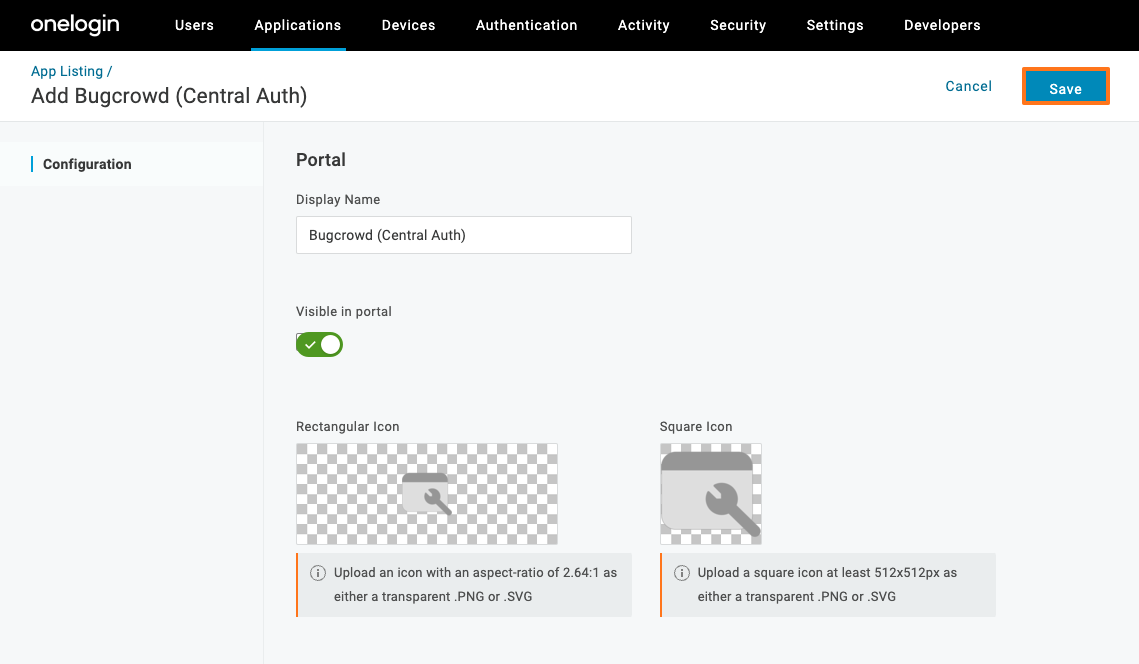
The Configuration page is displayed.
-
Modify any of the configuration settings that control how the Bugcrowd app appears in your portal.
-
Save the settings.
A new set of tabs appear that allow you to configure rules, parameters, SSO, access policies, and users for the Bugcrowd app.
-
Select the SSO tab.

-
Select X.509 Certificate (View Details) for additional information.
- Use SHA1
- X.509 Certificate
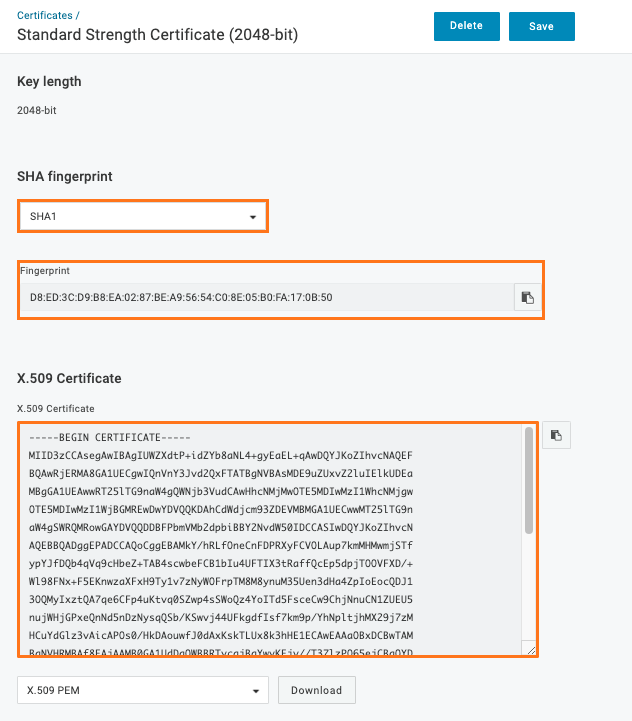
This page displays all the information that is required for adding to Crowdcontrol later. Make a note of the following information:
- X.509 certificate and its fingerprint
- Issuer URL
- SAML 2.0 endpoint
- SLO endpoint
Mapping OneLogin to Crowdcontrol
-
Navigate to the Single Sign-On screen in Crowdcontrol and scroll to the SAML Settings section.
-
Specify the OneLogin information that you noted in the earlier step.
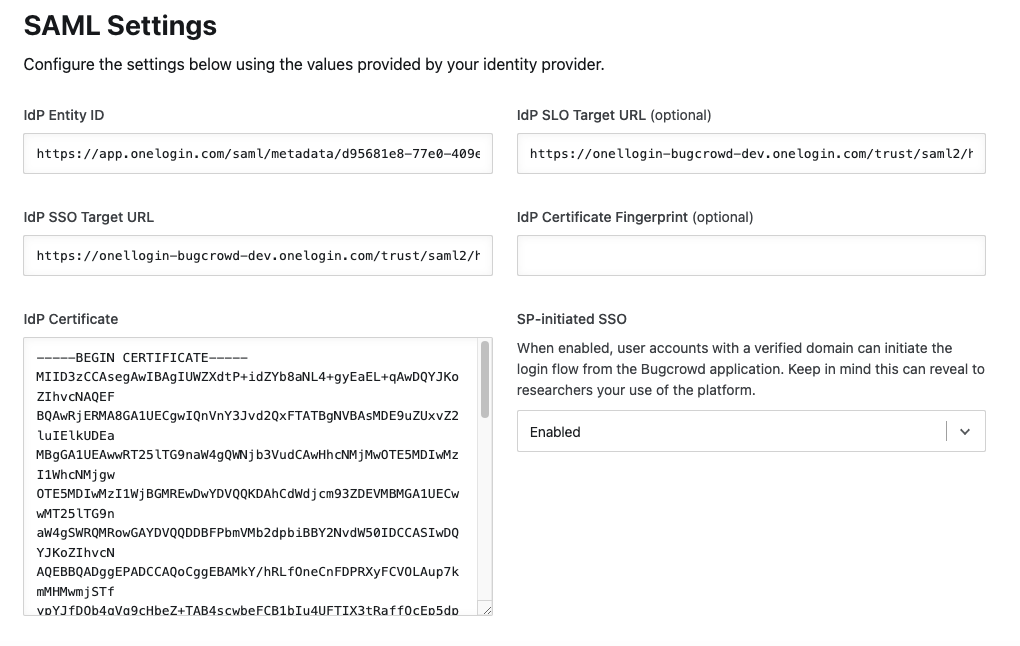
Single Logout: Bugcrowd only supports Identity Provider (IdP) initiated logouts, that is logging out of Bugcrowd will not log you out of your SSO provider.
The following table provides the Crowdcontrol fields mapped to OneLogin fields.
Crowdcontrol Field OneLogin Field IdP Certificate X.509 Certificate IdP Certificate Fingerprint Fingerprint IdP Entity ID Unresolved IdP SSO Target URL SAML 2.0 endpoint IdP SLO Target URL SLO endpoint When you add the X.509 certificate, you must copy and paste the entire contents of the certificate, including the BEGIN and END headers as shown.
-----BEGIN CERTIFICATE-----\nTTDMTSCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV\nm3LtH40luvg0sd0ng4evAT0mMYh4rdYDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX\naWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF \nt4c0fN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpR\nC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPUL\nB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq\nvA== -----END CERTIFICATE----- -
Save the settings. Crowdcontrol displays the SSO configuration for your program.
-
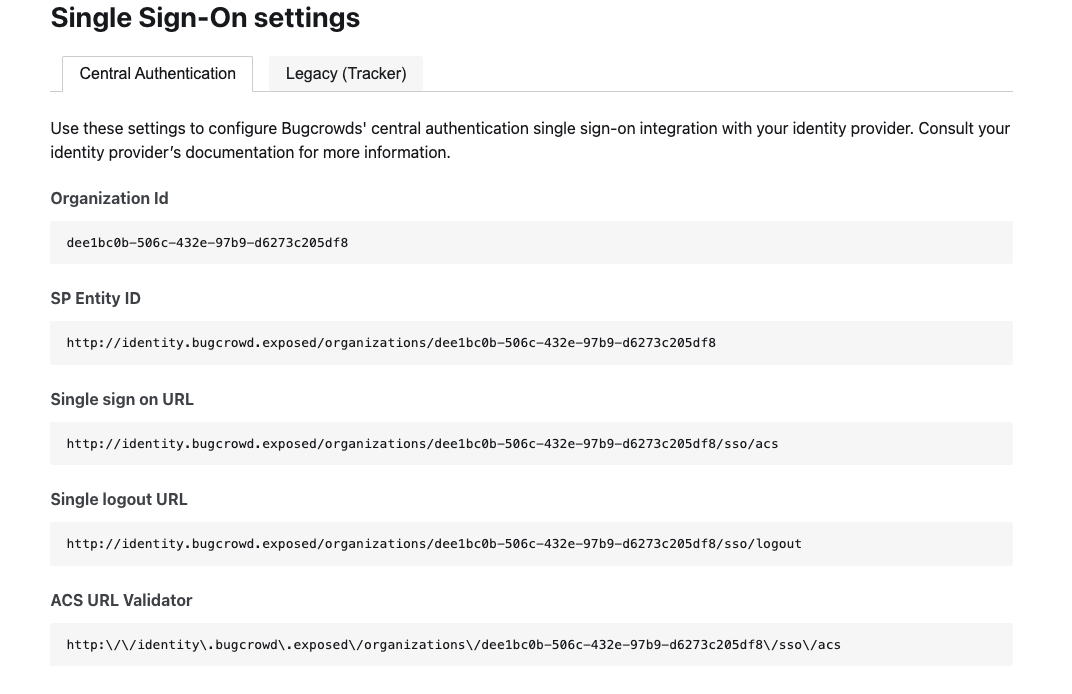
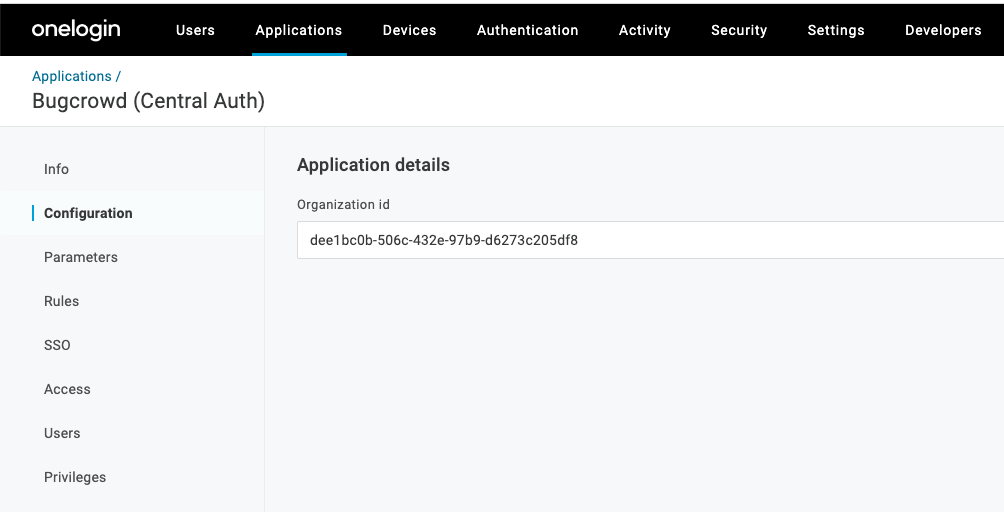
Copy the Organization Id. Make sure you are on Central Authentication tab.
-
Go back to your OneLogin account and navigate to the Bugcrowd Configuration tab. Paste the Organization id.
Domain verification is required for SSO to function properly. For more information, see verifying domain.
Logging in Using SSO
After you have enabled SSO, your team members can navigate to the Company Apps area of OneLogin and click the Bugcrowd app to log in. If SSO is set up properly, members will be logged in to Crowdcontrol.