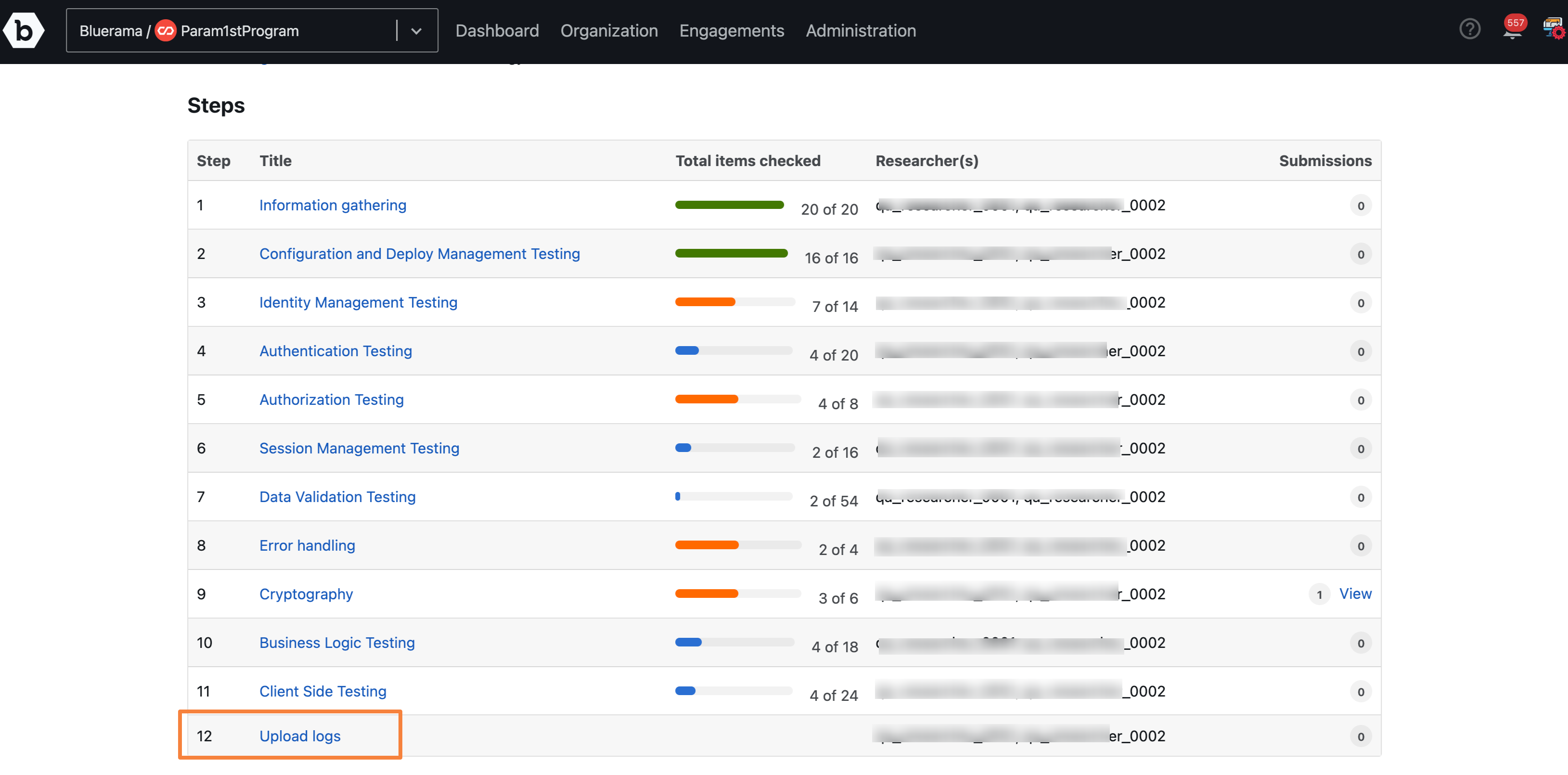
For any methodology based engagements (such as Pen Test), you can view the methodology steps followed while testing your assets. You can view the reported vulnerabilities, researchers added to an engagement, checklist summary, and step summary for every step in the methodology. You can also view notes that researchers have added for any step in the methodology. In the Upload logs step, you can view the log files that researchers have uploaded. Notes and attachments can be viewed both at the individual item level in a methodology step, as well as at the step summary level.
To view the methodology for a Pen Test, follow these steps:
-
Select the engagement from the Go to Security Program or Engagement drop-down.
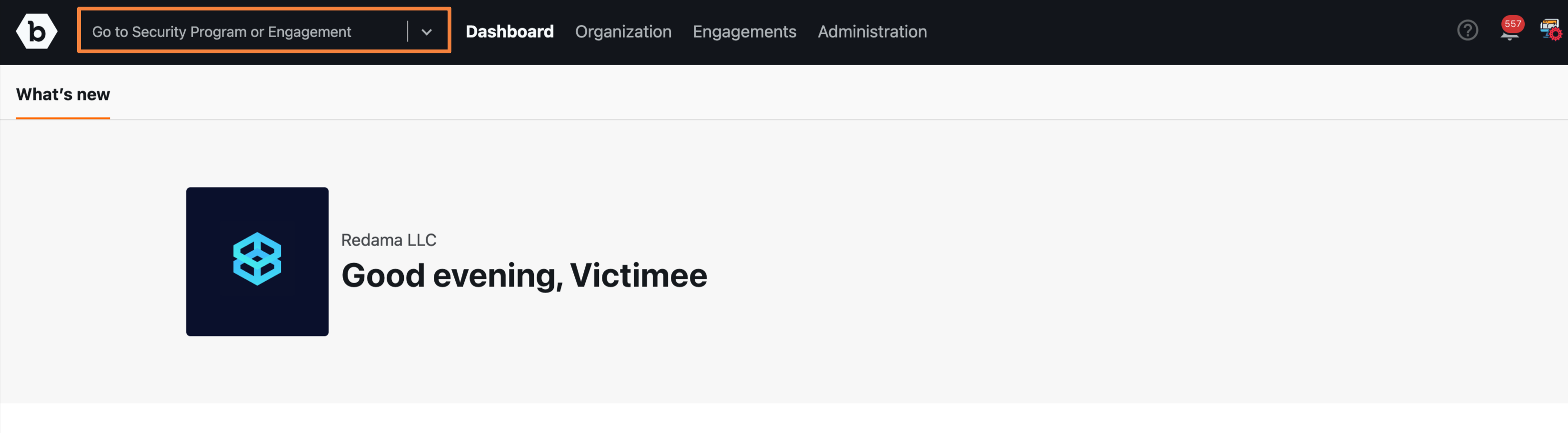
Alternatively, you can also select a security program and navigate to a linked pen test engagement.
-
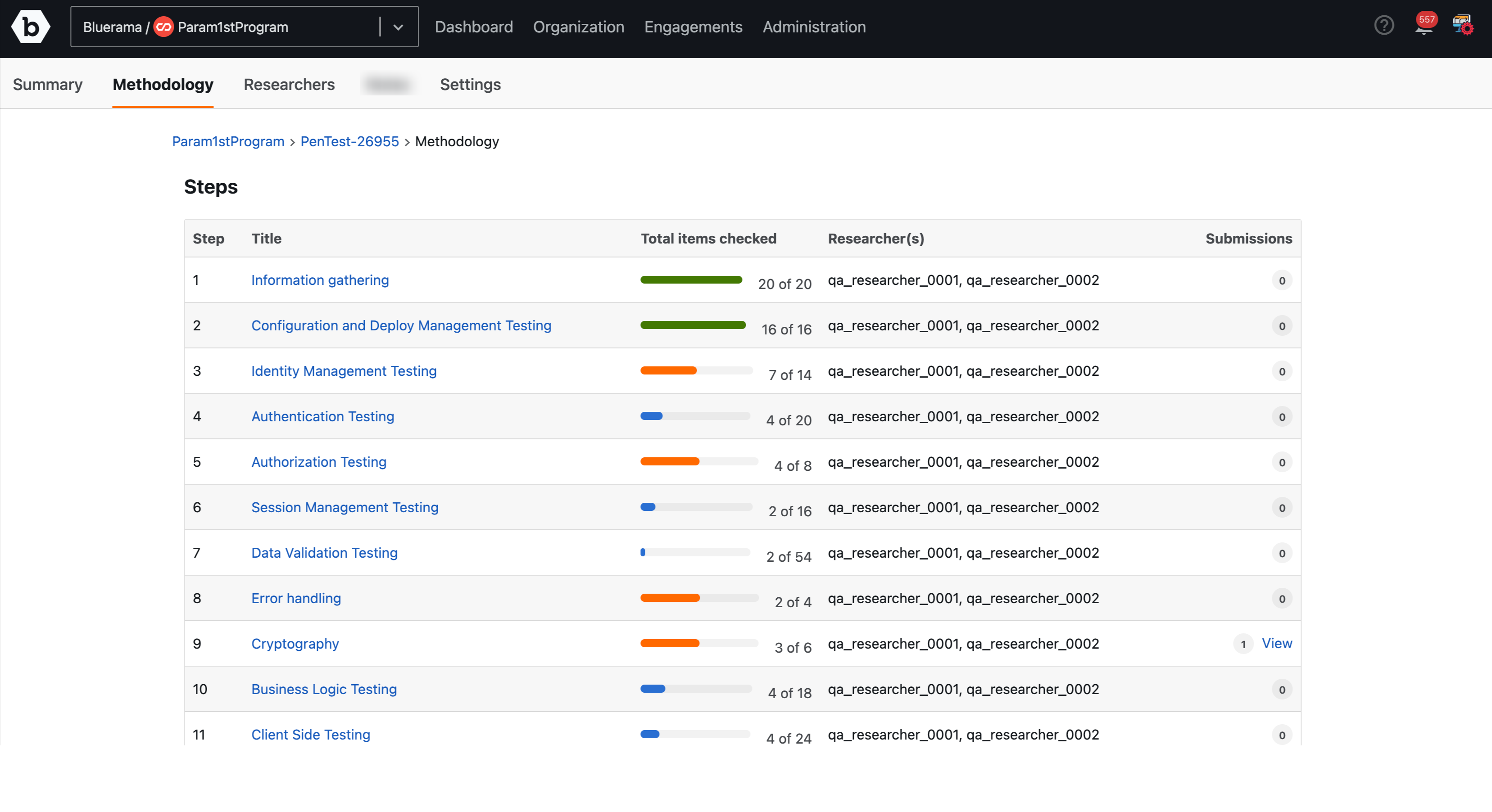
Click on Methodology. A list of all Steps in the methodology will be displayed.
-
Click on any step title link.
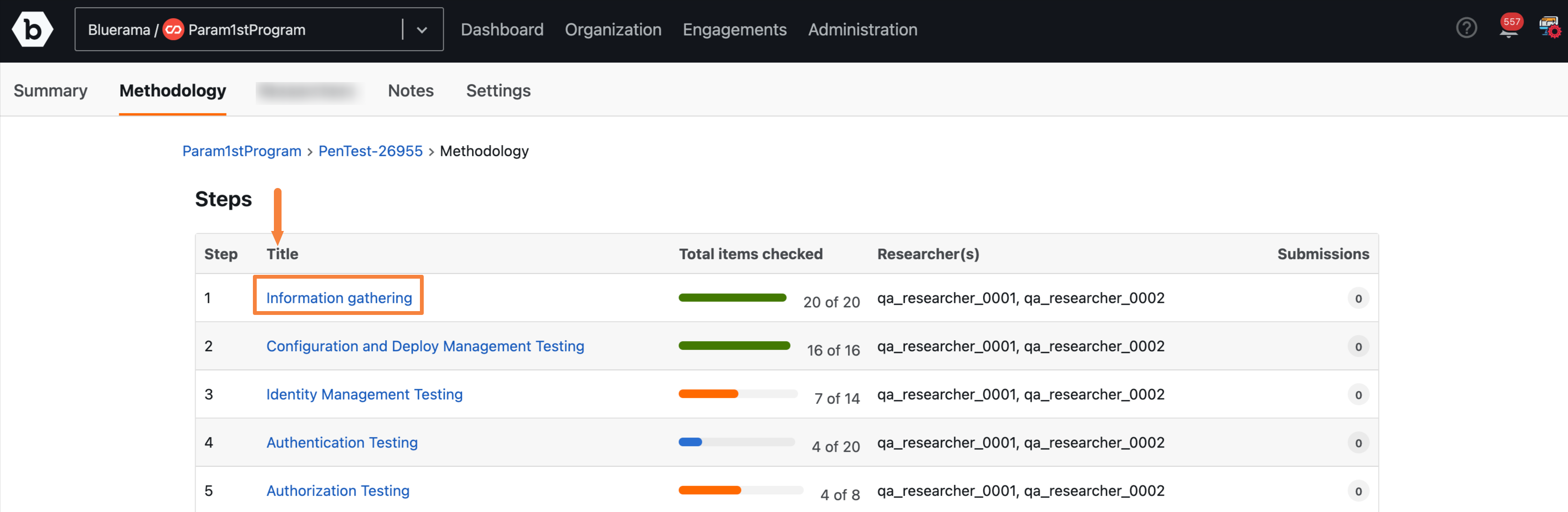
A drawer appears with the following information:
-
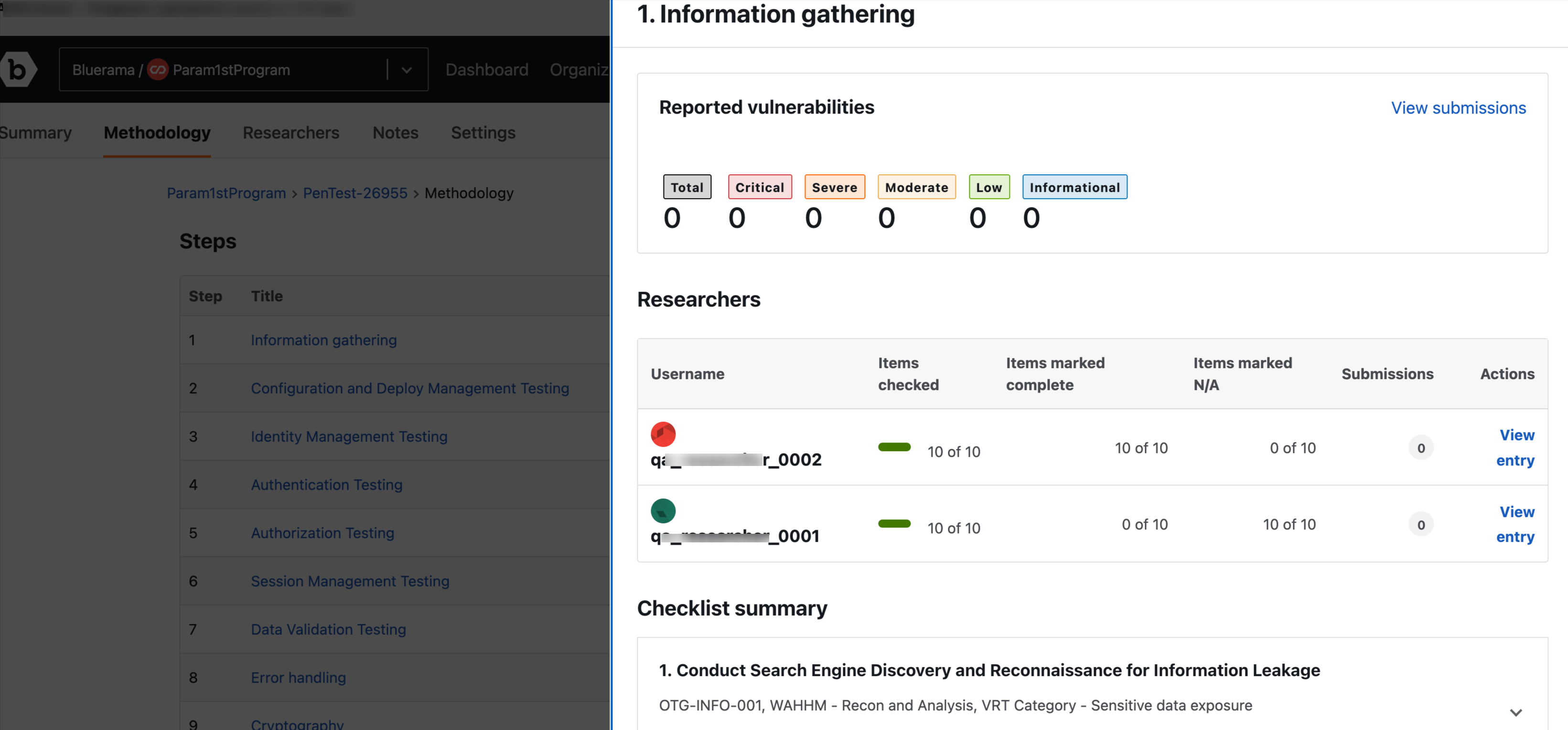
Reported vulnerabilities, researchers on the engagement, checklist summary, and step summary for the particular step.
-
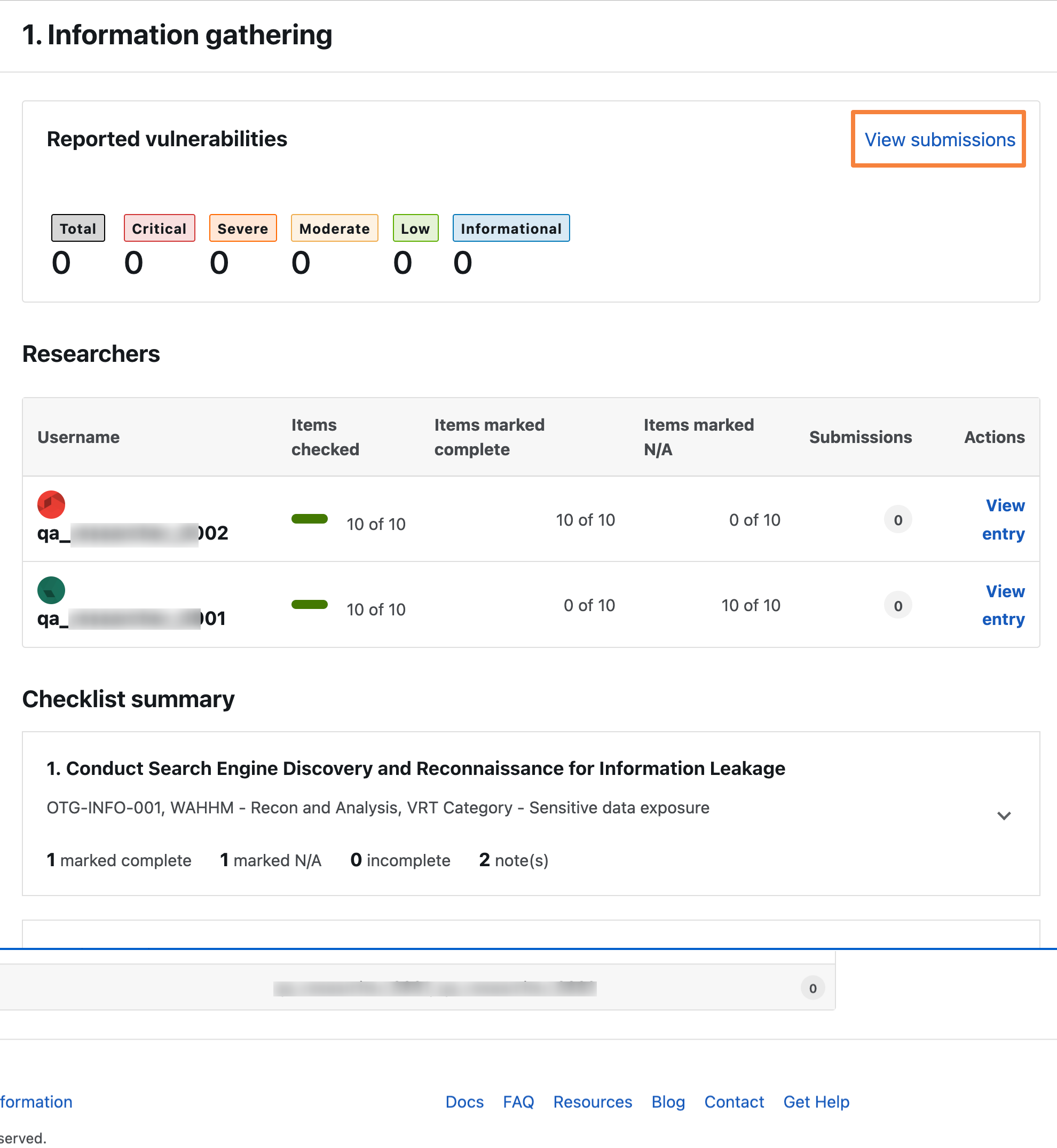
Click View submissions in the Reported vulnerability section to view all the submissions.
-
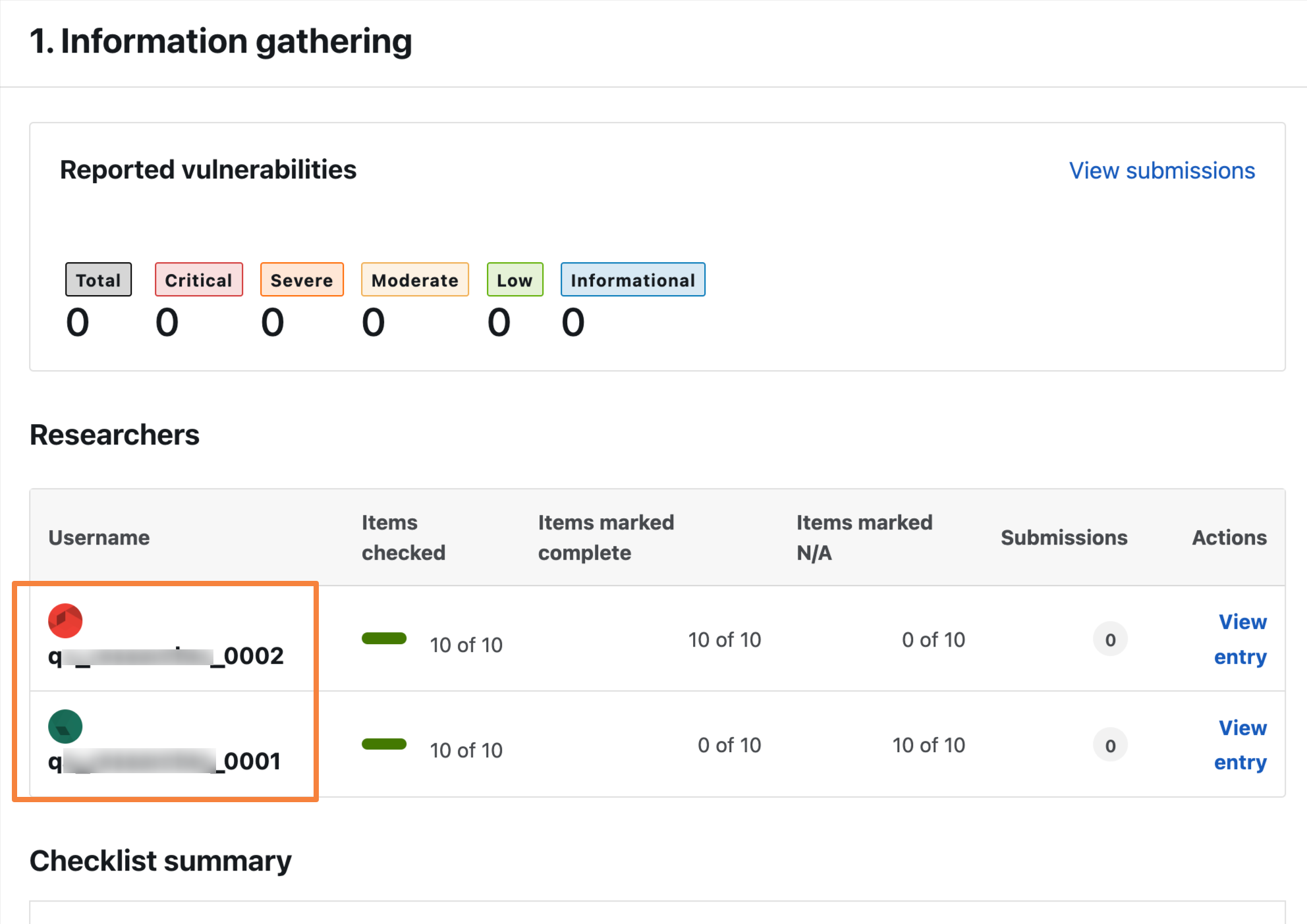
You will be able to see the list of researchers associated with the engagement.
-
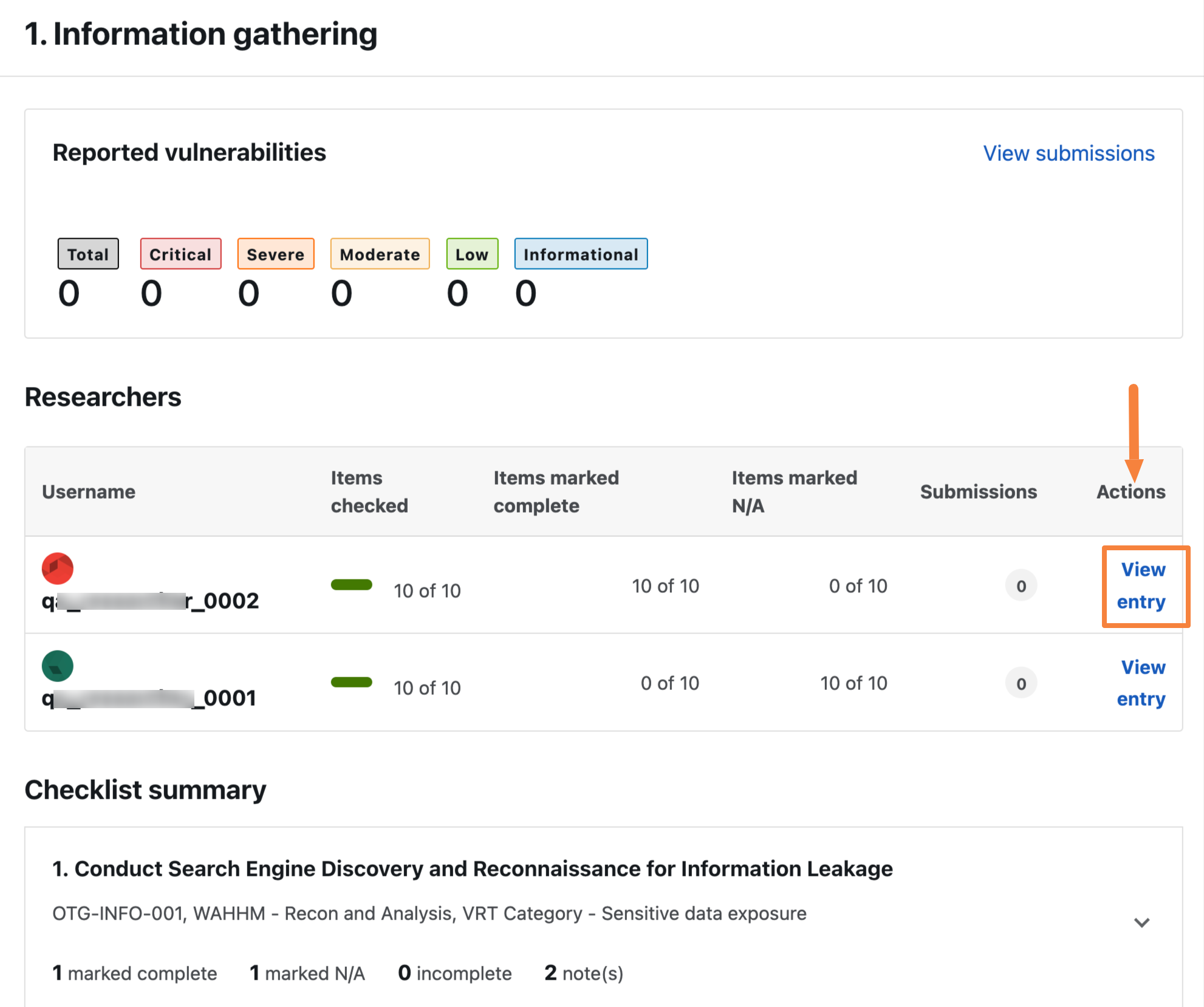
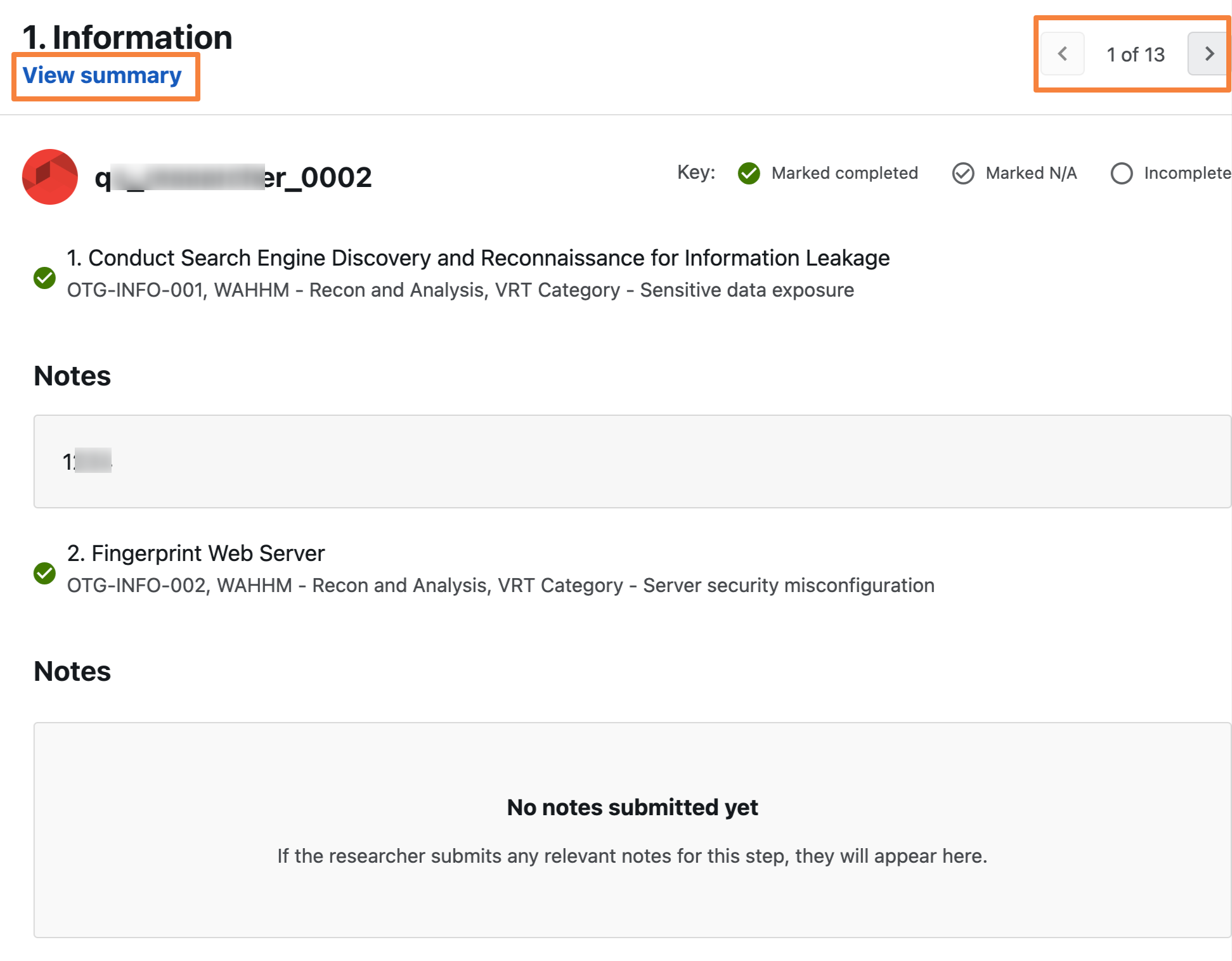
In Researchers section click View entry in the Actions column, to view relevant notes added for the selected step.
- You can view the notes for each step by navigating to the step from the pages list at top right. Clicking on View summary will take you back to the step page.
-
-
Click Upload logs to view the logs uploaded by researchers.