- Adding Bugcrowd to Your Okta Apps Portal
- Accessing SAML Information in Bugcrowd
- Adding SAML Information in Okta
- Mapping Okta to Crowdcontrol
- Logging in Using SSO
Bugcrowd offers a Security Assertion Markup Language (SAML) based Single Sign-On (SSO) integration with Okta to help you create an easy and centralized way to log in to Crowdcontrol. This document provides the steps to configure Okta.
Specific Role Required to Configure SSO: To configure SSO for your program, you must be an Organization Owner. Organization Owners can log in using Username and Password.
Adding Bugcrowd to Your Okta Apps Portal
-
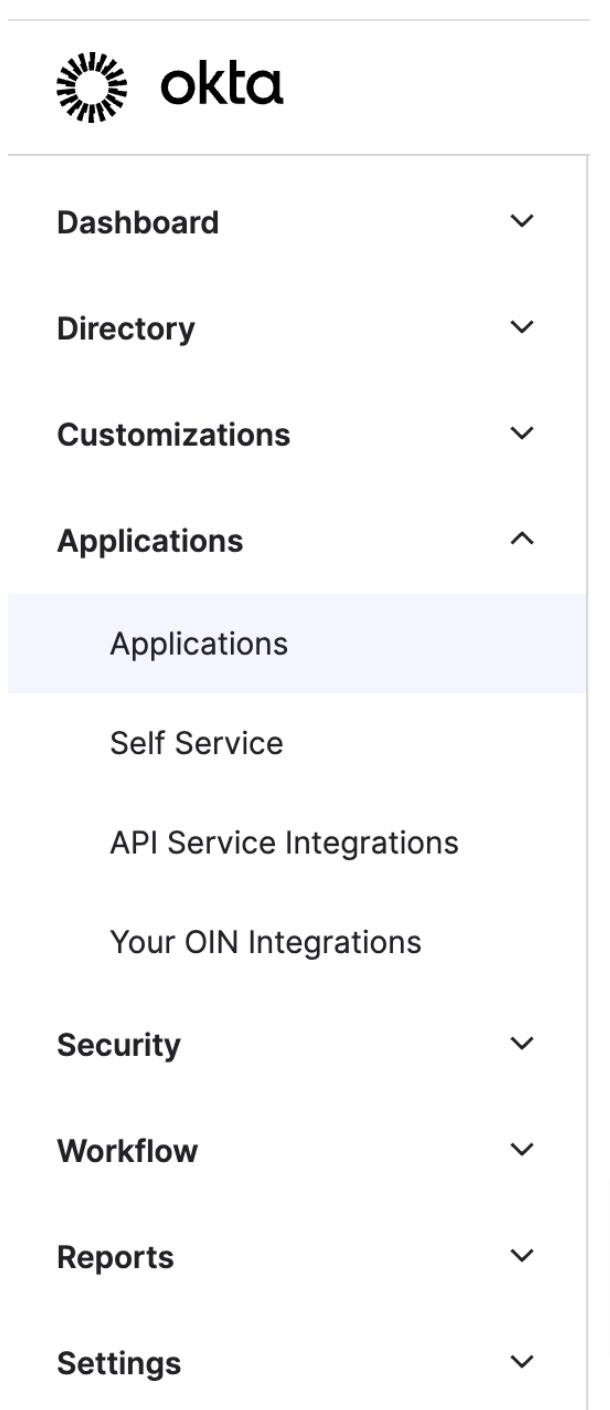
In Okta, expand Applications on the left panel and click Applications.
-
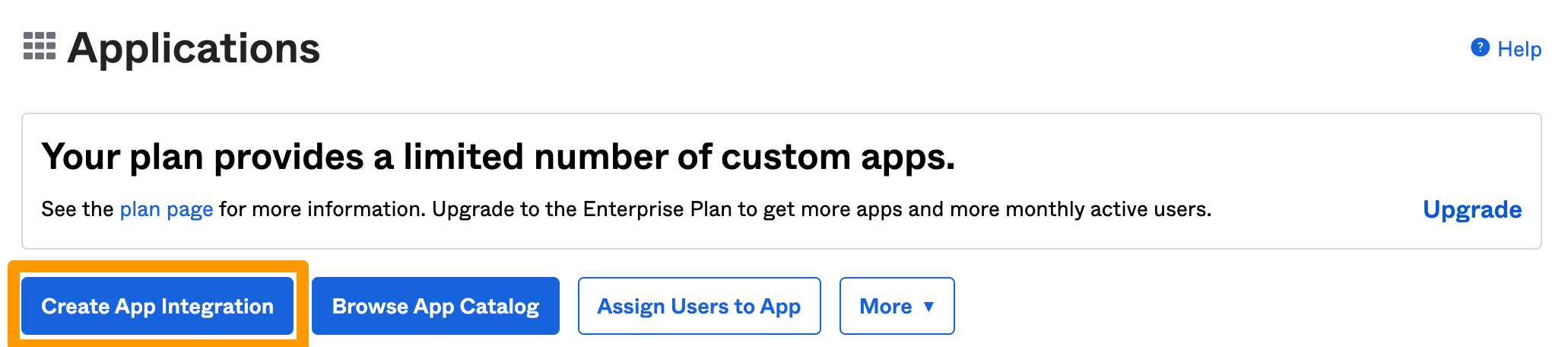
Click Create App Integration
The Create a new app integration window is displayed.
-
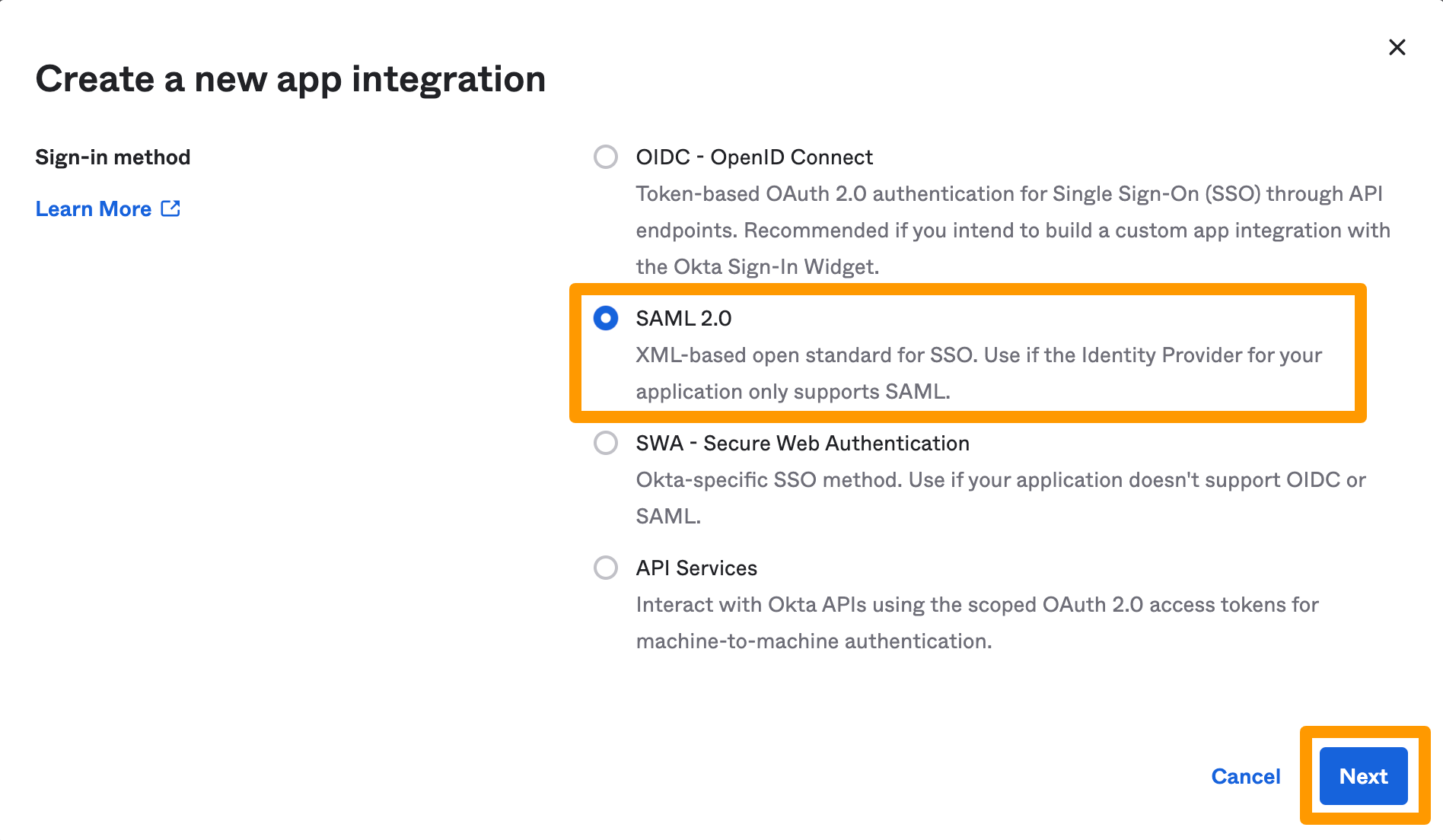
Select SAML 2.0 and click Next.
The Create SAML Integration page is displayed.
-
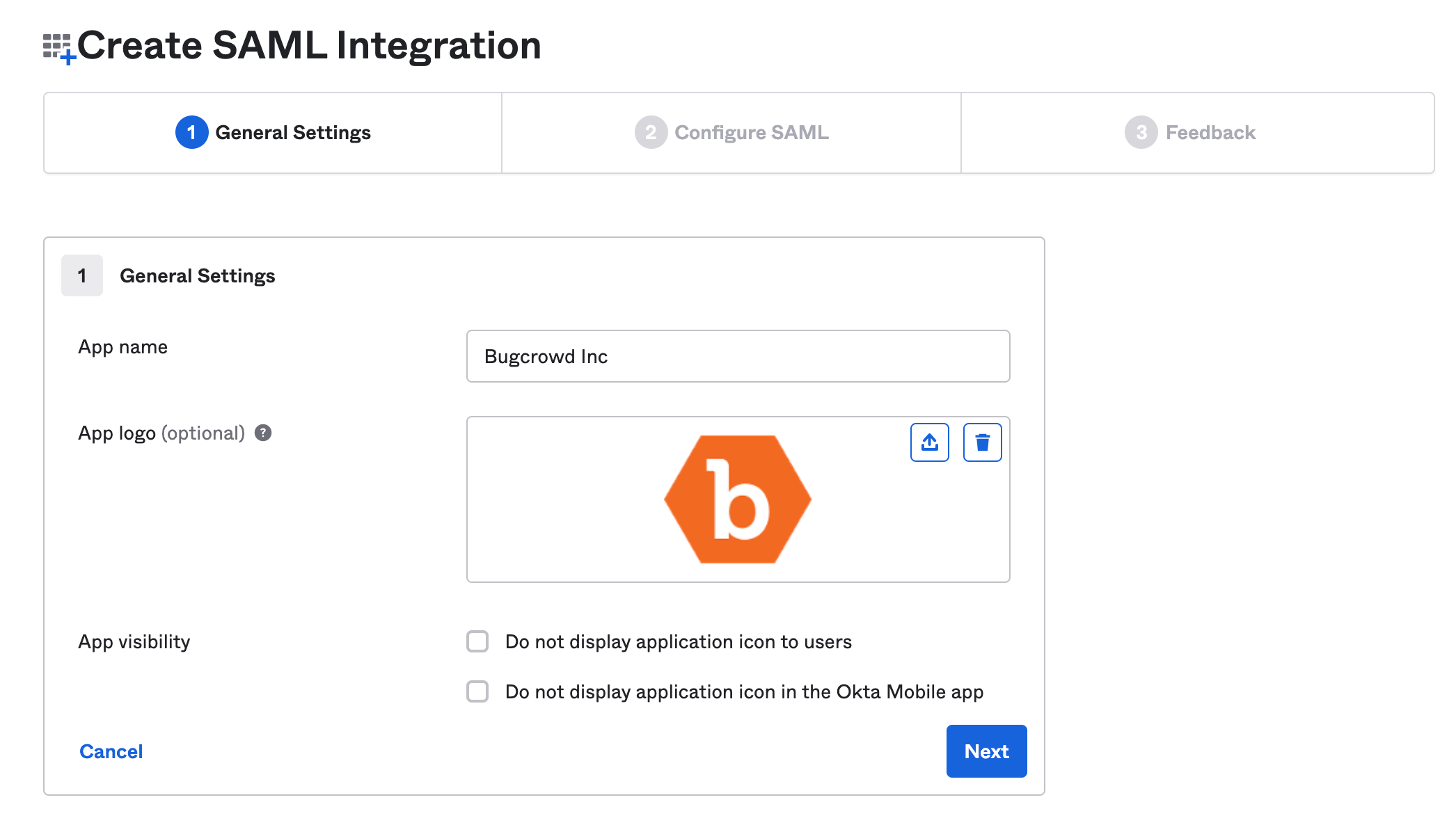
In General Settings, specify the following:
- App name: Enter Bugcrowd Inc as the app name.
- App logo: Click Browse and upload the Bugcrowd logo.
-
Click Next.
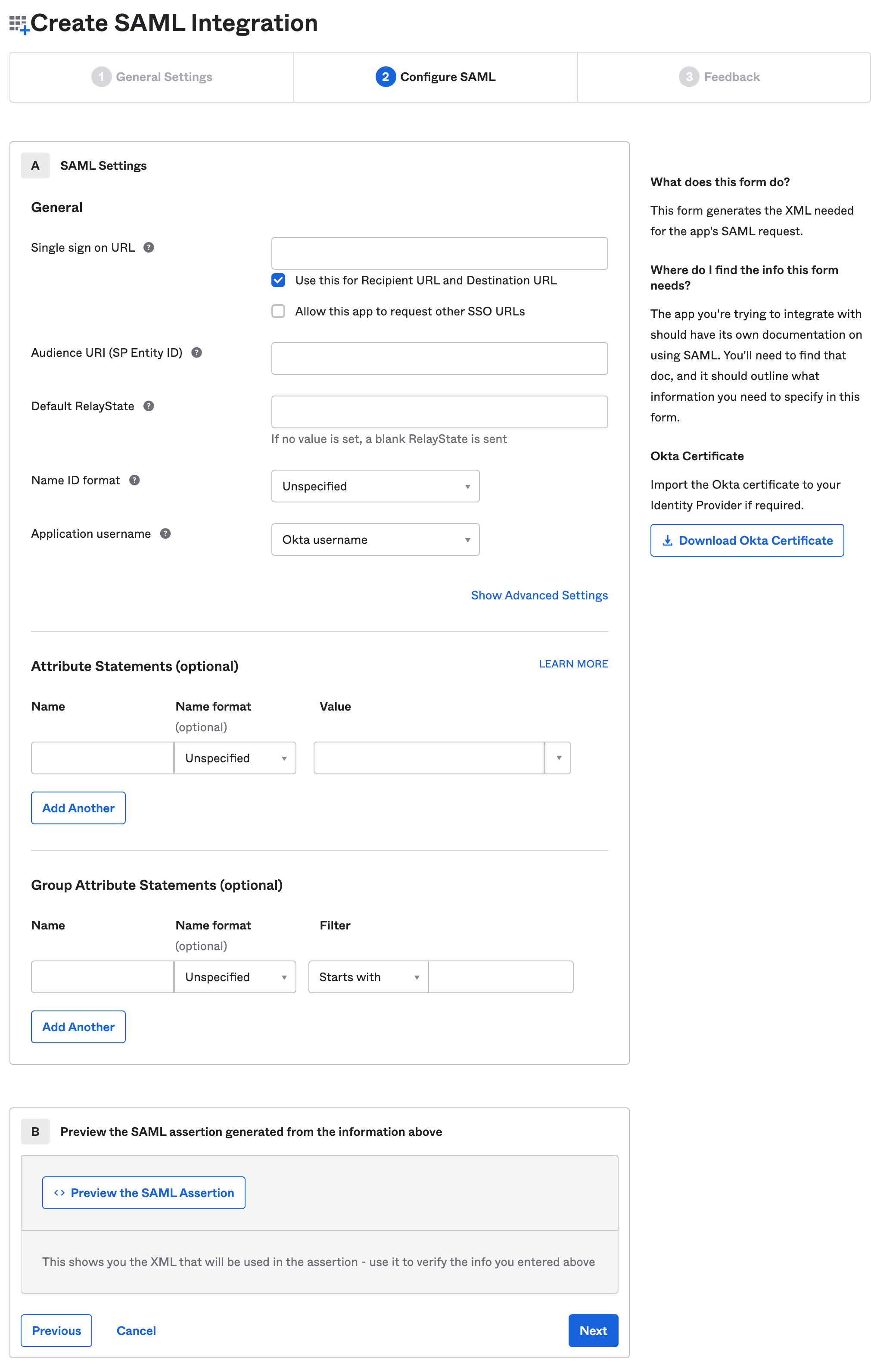
The SAML Settings page is displayed.
To specify the information for this screen, you must access your Bugcrowd account.
Accessing SAML Information in Bugcrowd
-
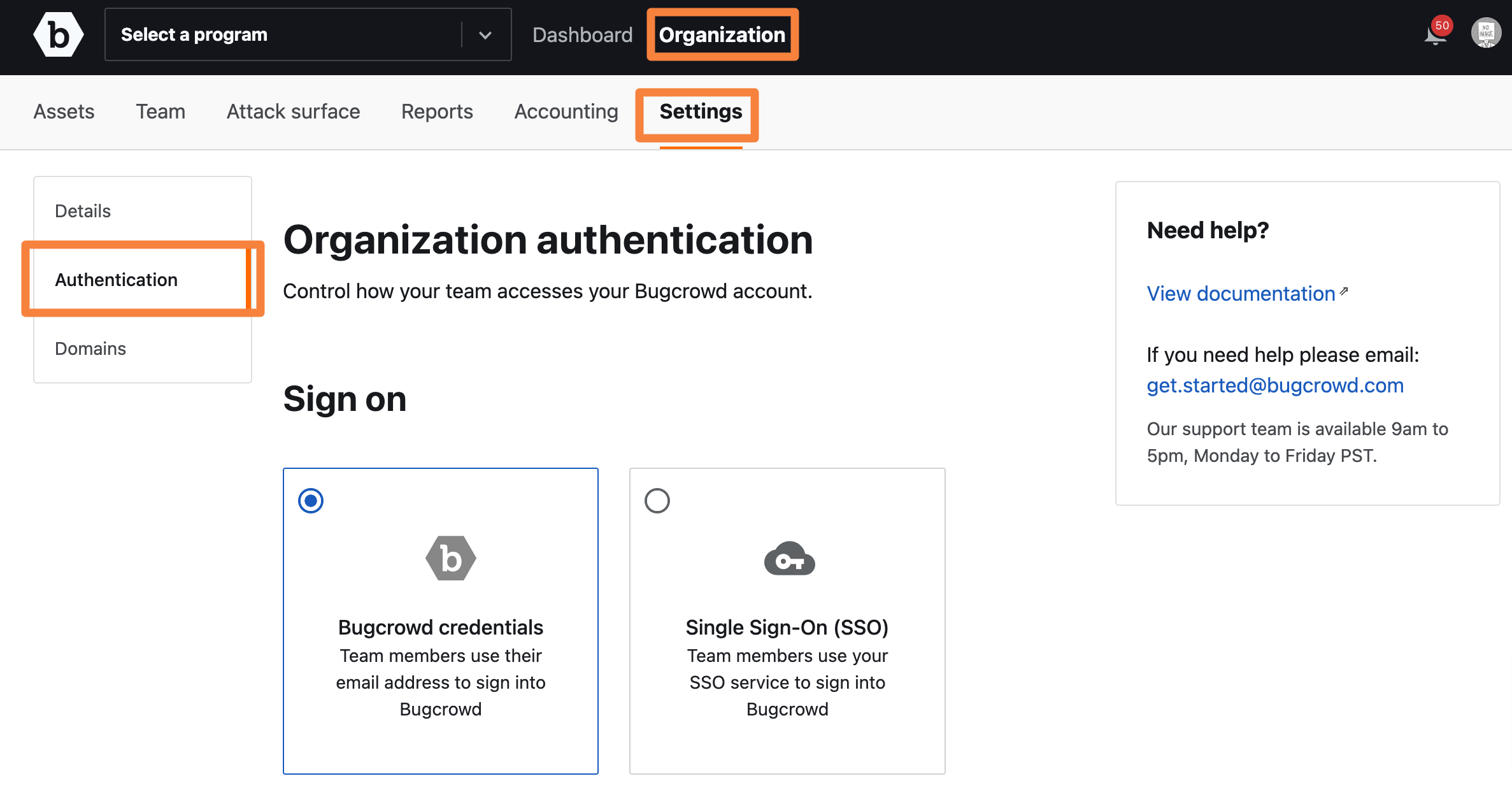
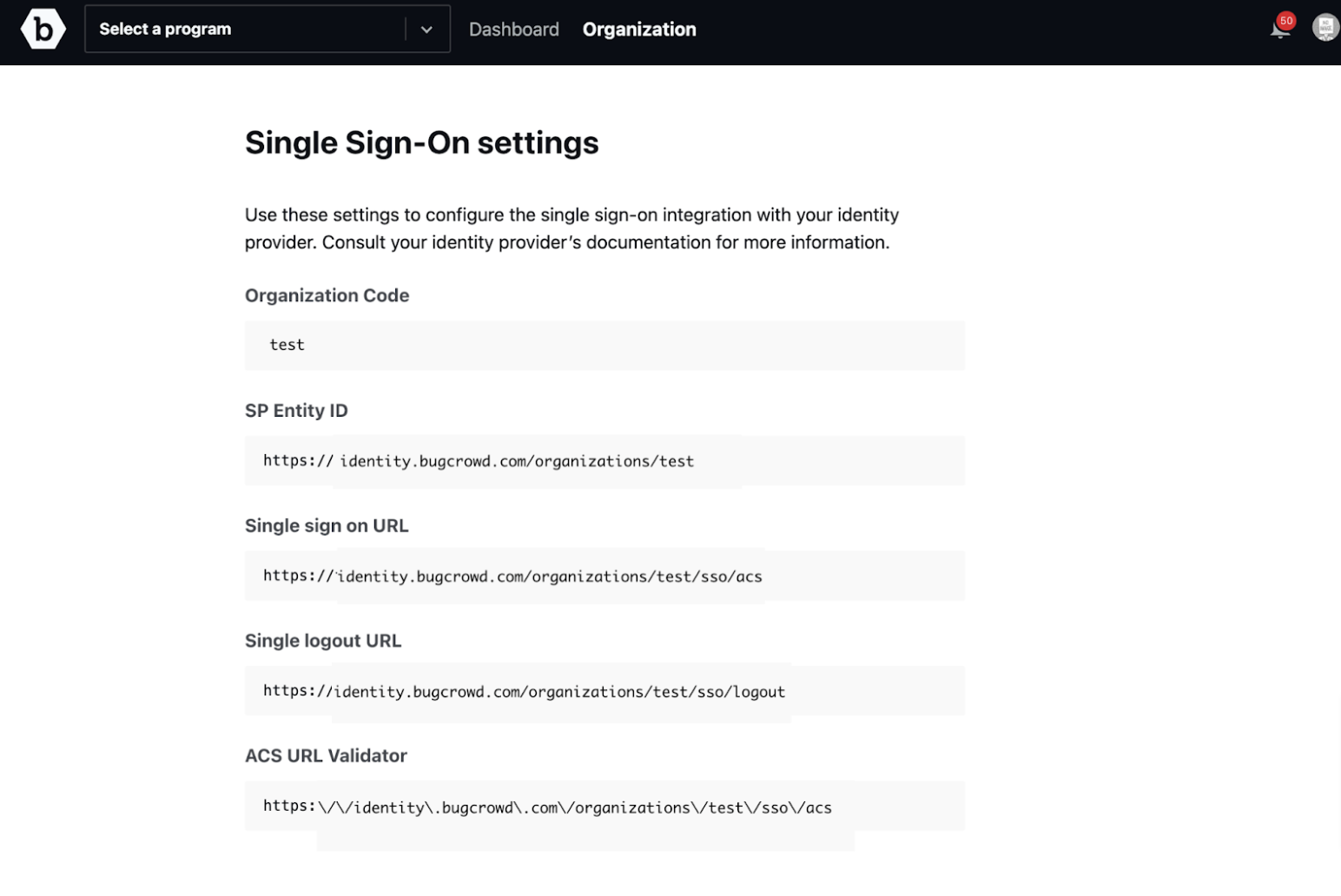
In Crowdcontrol, under Organization, click on Settings and then Authentication.
-
Click Single Sign-on (SSO).
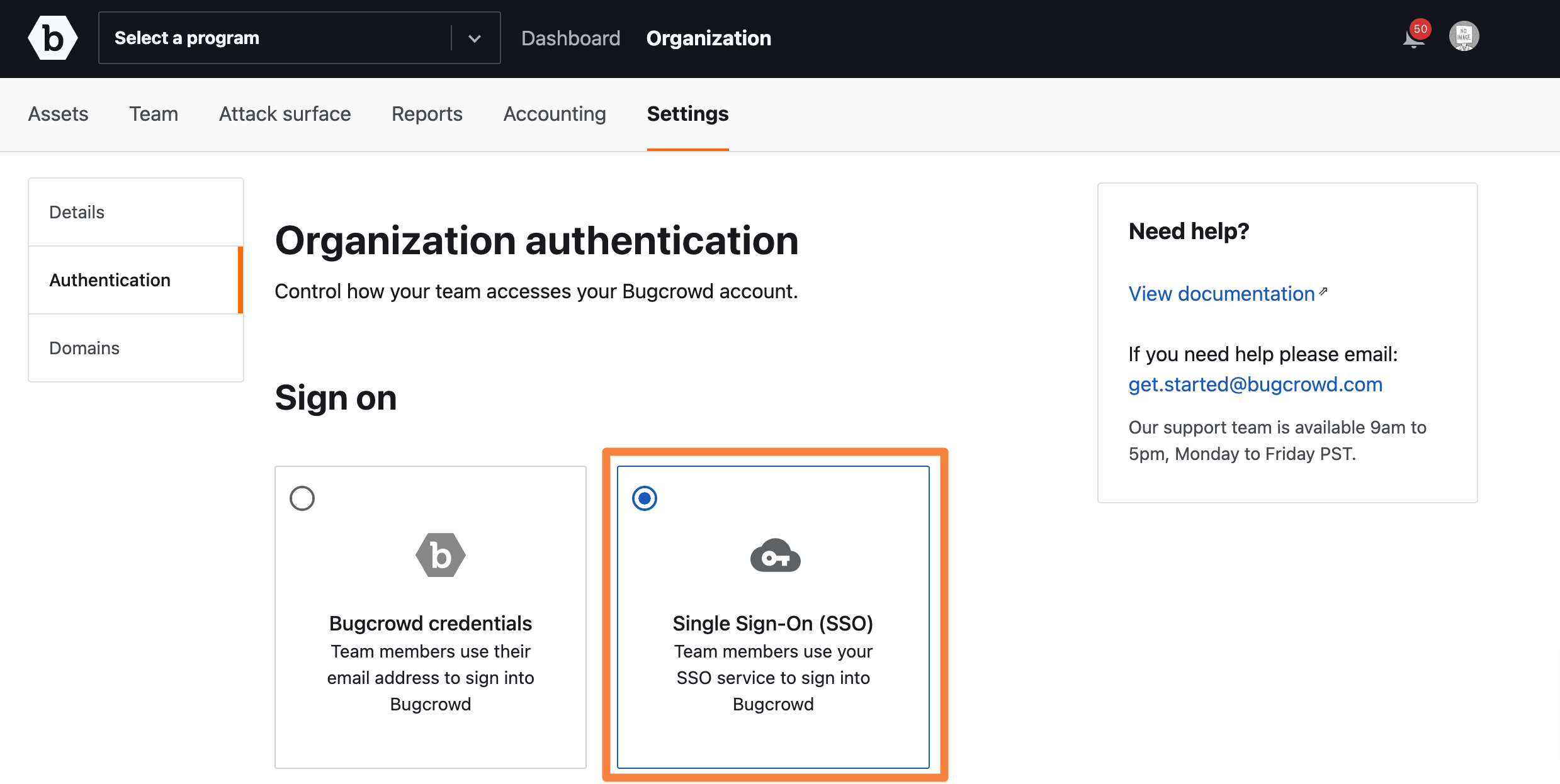
The SSO Configuration for Demo Organization is displayed.
-
Make a note of the Single sign on URL and SP Entity ID.
Single Logout: Bugcrowd only supports logouts Identity Provider (IdP) initiated logouts, that is logging out of Bugcrowd will not log you out of your SSO provider.
-
Pause the screen and go to the next step.
Adding SAML Information in Okta
-
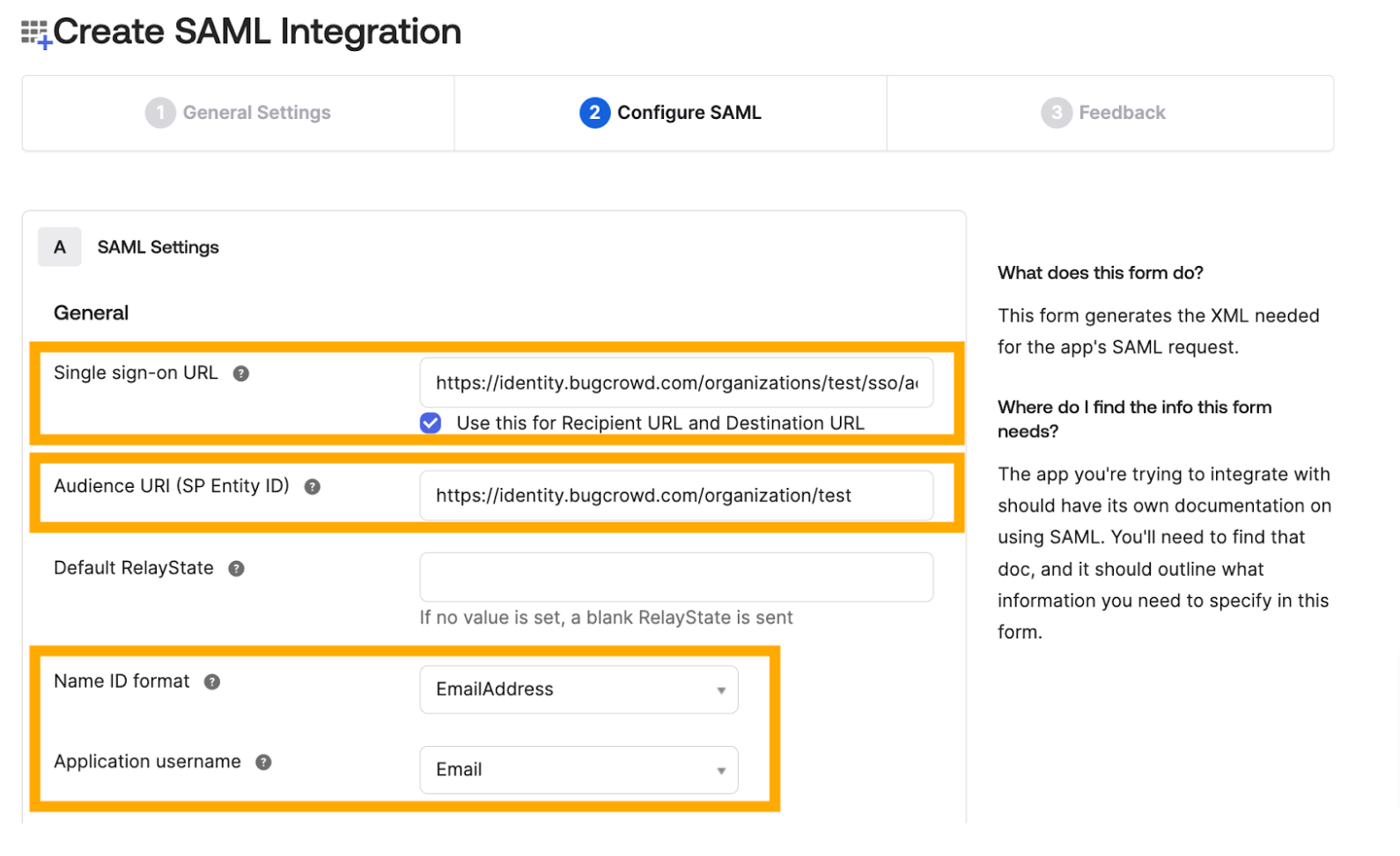
Go back to Okta > Configure SAML page (last step in the first section).

-
Specify the following information from your Bugcrowd account (Settings > Authentication > Single Sign-on (SSO))
- Single sign on URL: Paste the Single Sign on URL from your Bugcrowd account.
- Audience URI (SP Entity ID): Paste the SP Entity ID from your Bugcrowd account.
- Name ID format: Select EmailAddress.
- Application Username: Select Email.
-
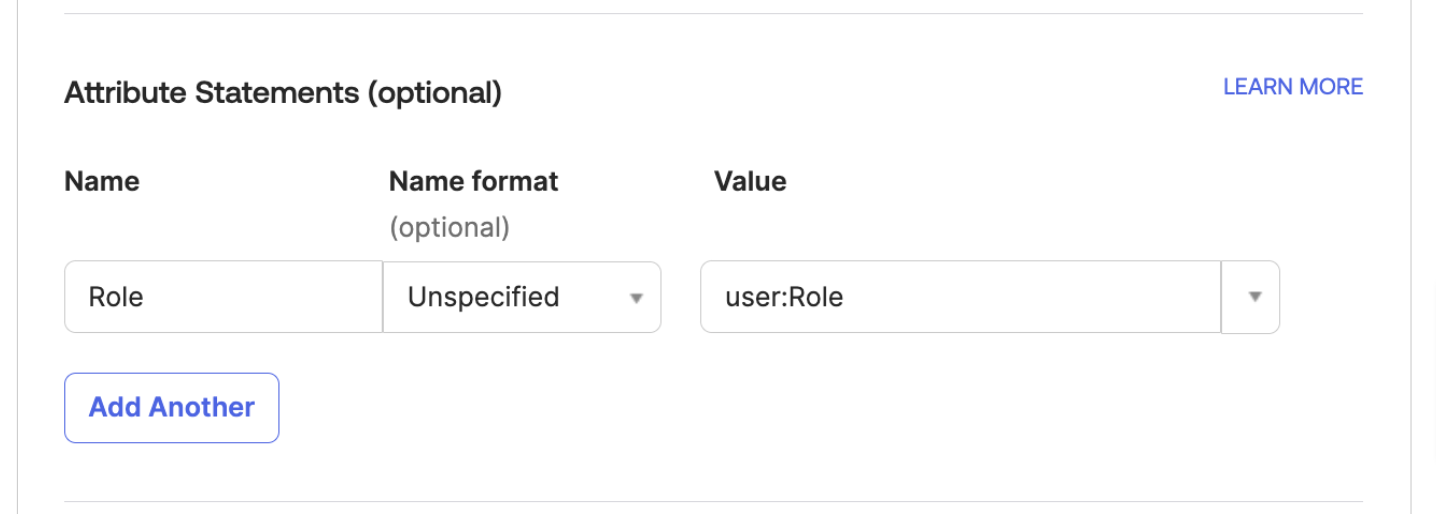
In Attribute Statements section, specify the following:
- Name: Select Role
- Value: Select user:Role
-
Click Next.
The Feedback page is displayed.
-
Select This is an internal app that we have created and click Finish.
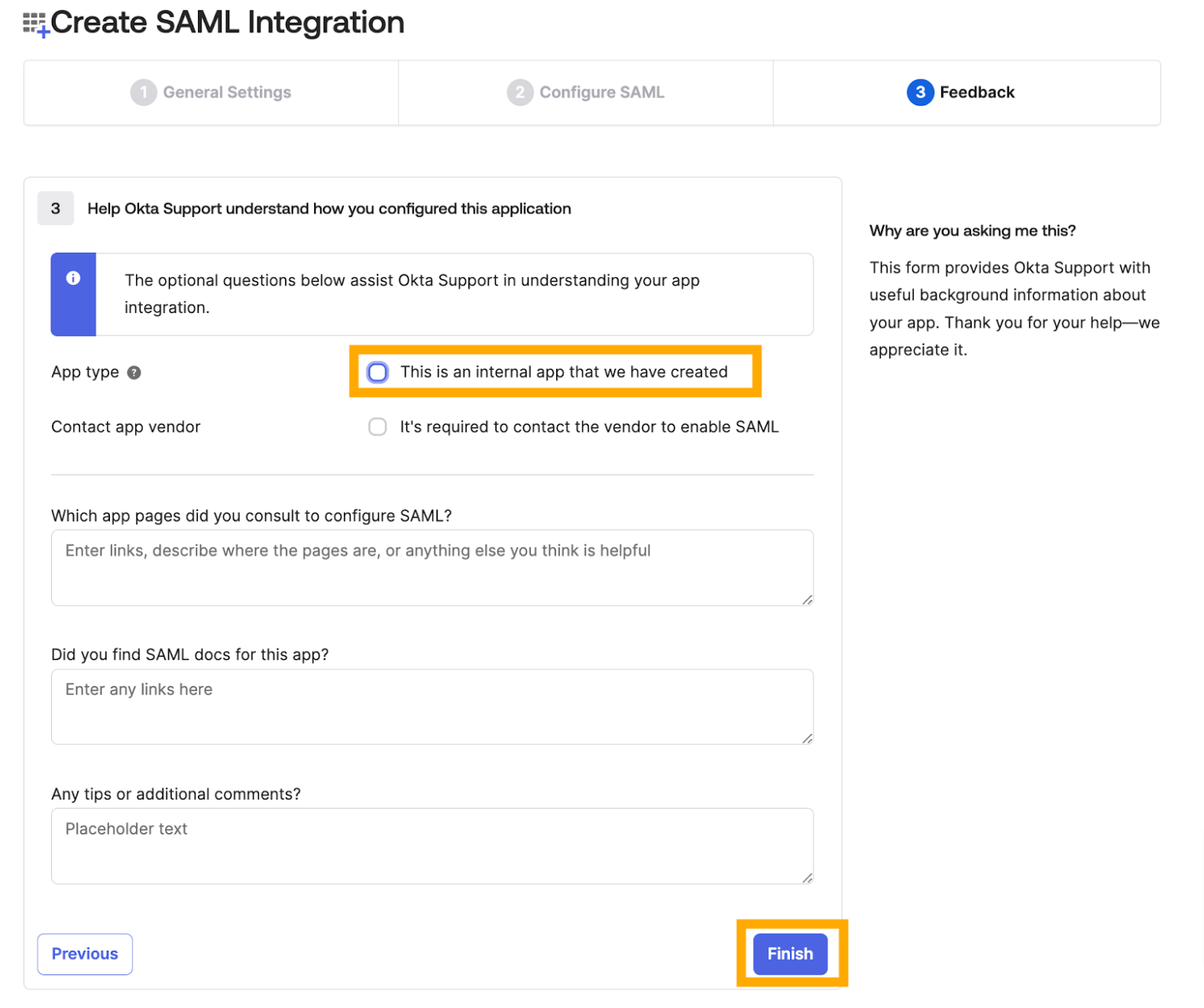
The Sign-on settings page is displayed. Next, you must map Okta to Crowdcontrol.
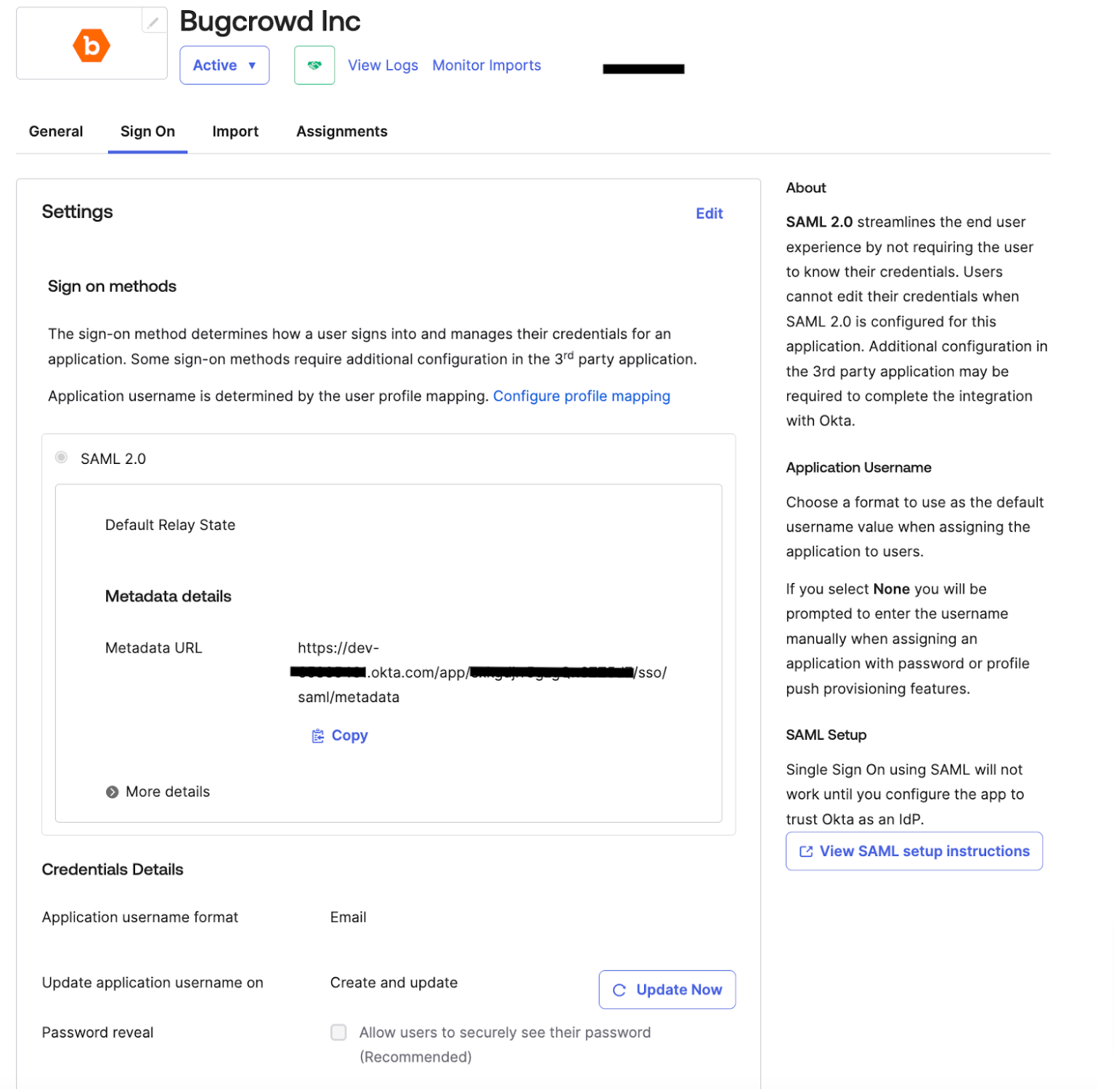
Mapping Okta to Crowdcontrol
-
Click View SAML setup instructions.
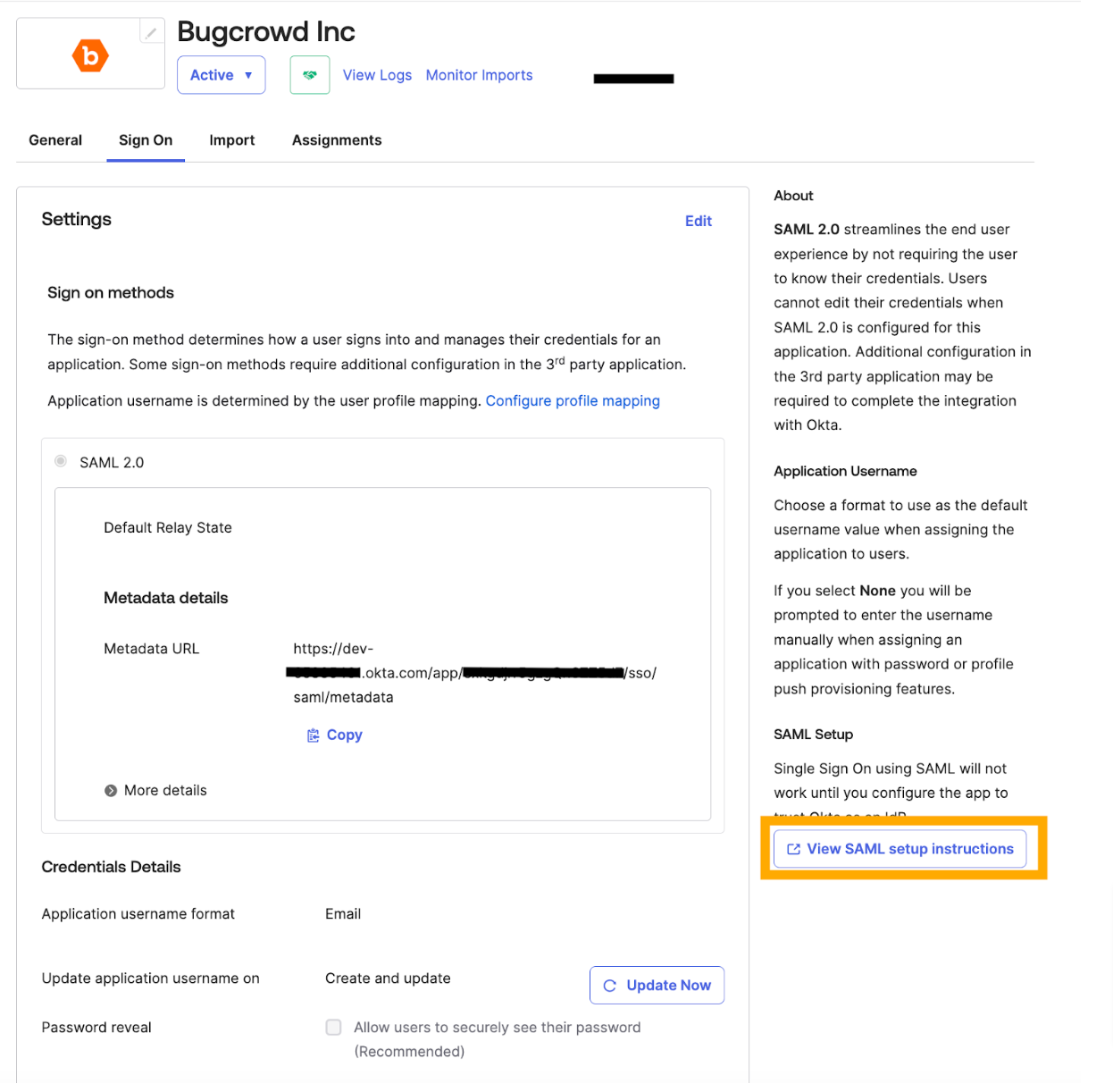
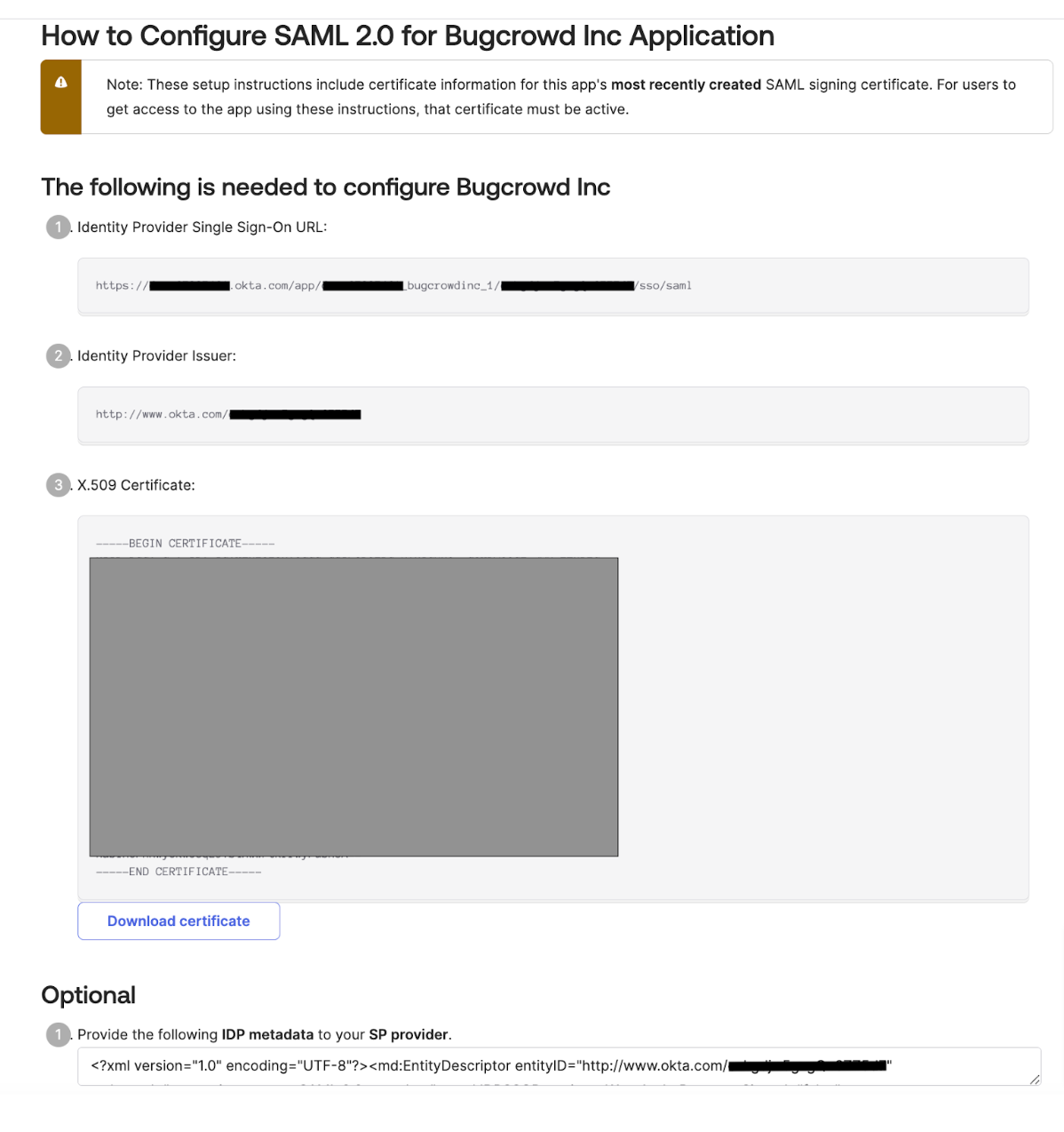
The How to Configure SAML 2.0 for Bugcrowd Inc. Application screen is displayed.
-
Make a note of the following information:
- Identity Provider Single Sign-On URL
- Identity Provider Issuer
- X.509 Certificate
-
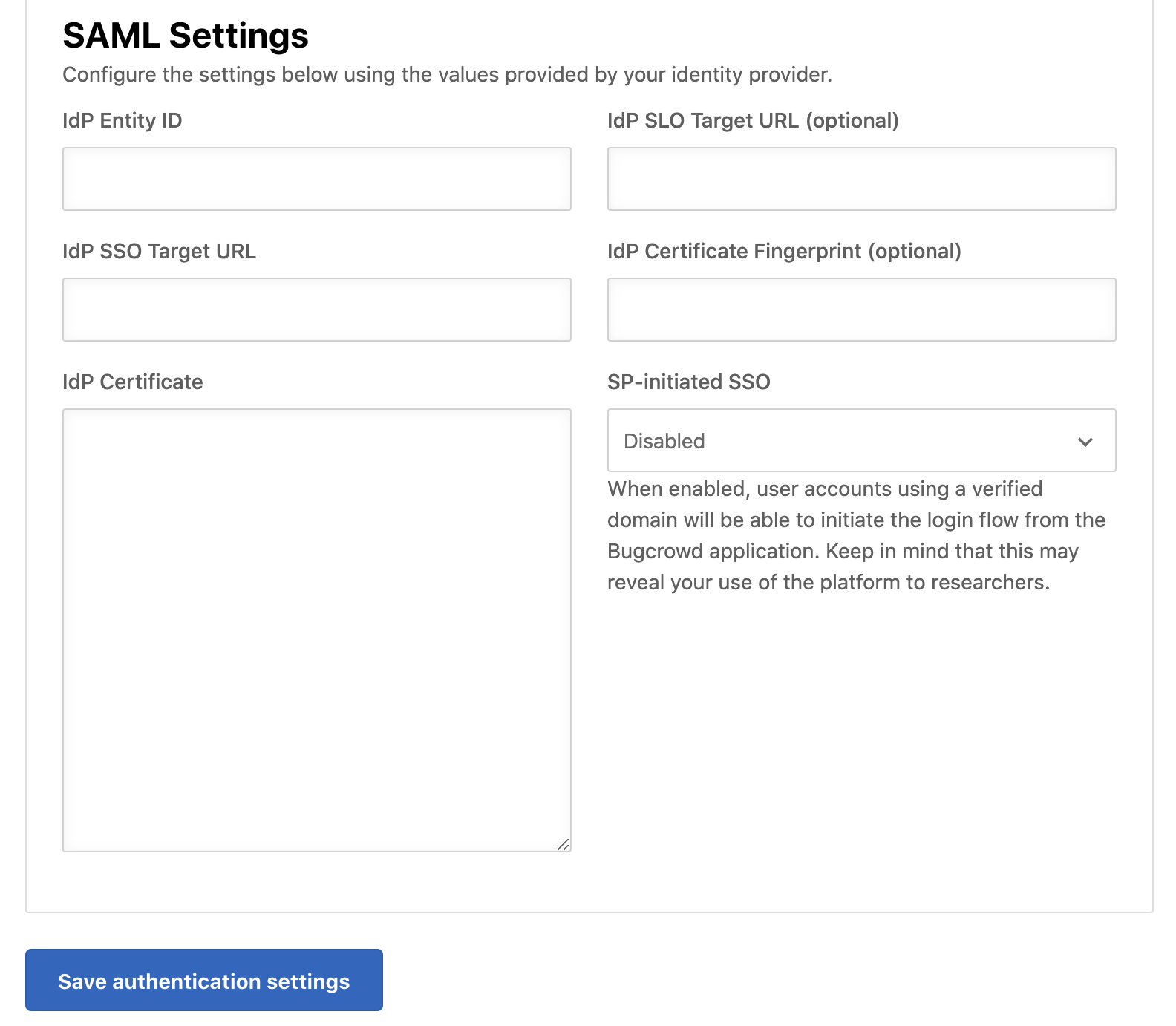
Navigate to the Single Sign-On screen in Crowdcontrol and scroll to the SAML Settings section.
-
Specify the following information from Okta:
- IdP Entity ID: Paste the Identity Provider Issuer information from Okta.
- IdP SSO Target URL and IdP SLO Target URL: Paste the Identity Provider Single Sign-On URL information from Okta.
- IdP Certificate: Paste the X.509 Certificate information from Okta.
-
Click Save authentication settings to save the information.
Domain verification is required for SSO to function properly. For more information, see verifying domain.
Logging in Using SSO
After you have enabled SSO, your team members can log into Okta and click the Bugcrowd app to log in. If SSO is set up properly, members will be logged in to Crowdcontrol.